Systems with prevention, defense, and monitoring to deter attacks
Rapidly develop containerized applications with the proper precautions against potential risks. Employ a comprehensive approach to securing containers, Kubernetes, and cloud environments.
Secure Kubernetes across multiple clouds
Easily monitor containers, Kubernetes, and the cloud with no agents needed. Analyze and prioritize risk with the SecLogic Security Graph. Empower developers and security to address containerized application issues early on.
Transparency
Scan all your managed and self-managed Kubernetes, serverless, and standalone containers running on virtual machines to understand your containerized environments completely.
Risk assessment
Use Security Graph to analyze data and prevent attacks in containers, hosts, clouds, and Kubernetes. Identify risks, vulnerabilities, and excessive permissions for system security.
Move to the left.
Work together with your team to ensure secure container images during the SDLC, covering Kubernetes YAML files, Docker files, and Terraform scans. Avoid any security issues during deployment.
Secure container images throughout their lifecycle.
Code
Scan Docker, Kubernetes YAMLs, Helm with SecLogic Guardrails
Build and Store
Use Seclogic Guardrails to scan container images along with registry scanning
Deploy
Prevent security threats using SecLogic Admission Controller
Run
Just checking out those running containers without any fancy agent
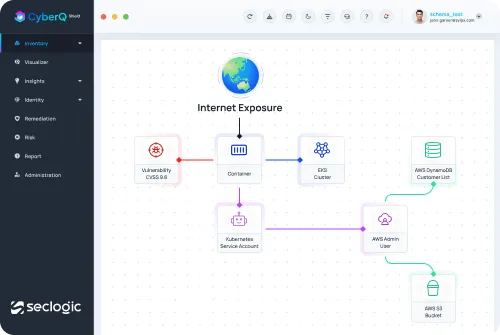
Graph risk analysis and prioritization
Managing the security of Kubernetes is automatic with KSPM
Ongoing observation
Regularly check Kubernetes clusters for errors and advise on solutions to reduce risks and make the clusters more secure.
Evaluate compliance with rules and laws
Receive security reports for Kubernetes environments and ensure compliance with CIS Foundation Benchmarks for EKS, AKS, and GKE.
Rules that are included and ones that are personalized
One can leverage the built-in rules and develop tailored rules utilizing OPA’s Rego querying language.
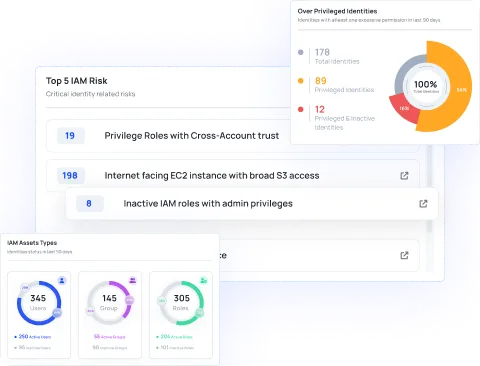
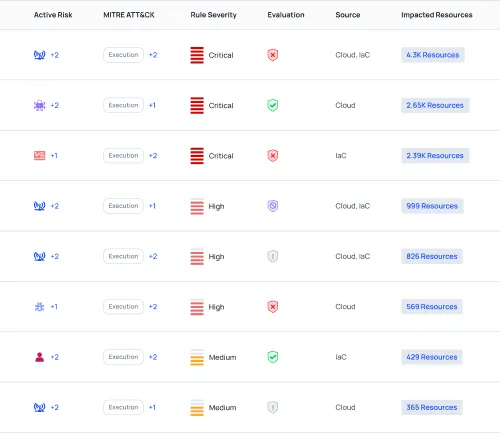
Ensure safety measures during development
Make sure all your IaC files (for Dockerfiles, Kubernetes YAML files, and Helm charts) are free of errors and potential security risks. Implement a single security policy for your cloud and Kubernetes development, and halt any builds that violate it. Before deploying to the cluster, confirm that container images align with the security policy.
Connect in minutes without agents
Complete security for AWS, Azure, GCP, OCI, Alibaba Cloud, VMware vSphere, Kubernetes, and Red Hat Openshift. Meet your new partner in cloud security.