Managing Cloud Infrastructure Entitlement Management
CyberQ Shield checks how much access each Identity have to your cloud and automatically generates policy basis what they really need.
Expertly Handle Your Cloud Entitlements
CyberQ Shield analyzes cloud system entitlements and permissions to help teams understand identity-related risks. Scans detect exposed secrets and lateral paths that could compromise sensitive assets, followed by automated remedial suggestions and policies prioritizing least privilege.
Adjust permissions to fit better.
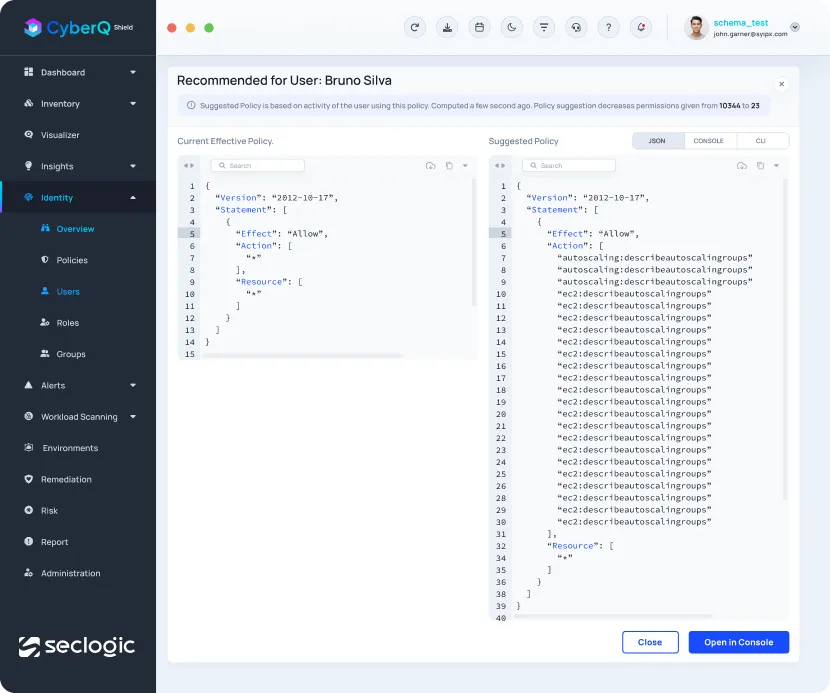
Monitor human and service identities, use auto-generated least privilege suggestions to manage access and entitlements.
Analyze Permissions
SecLogic maps effective access for all principals and resources, considering cloud-native mitigating controls like boundaries, ACLs, and SCPs.
Secrets and movement.
Our service easily detects leaked secrets/credentials and prevents unauthorized access to assets/accounts, without additional agents or complexity.
Enforce least privilege for your clouds
Seclogic analyzes permissions, helps teams understand access, and strengthens security policies. Granular analysis provides visibility and identifies vulnerabilities, allowing proactive risk mitigation. Informed decisions empower organizations to safeguard data from breaches.
This feature automatically analyzes un-used identities actions and generates optimized policy using the principal of least privilege methodology.
A built-in knowledge base provides quick answers to frequently asked customer questions, reducing the workload on support teams and improving customer satisfaction.
Go further than CIEM
Identify the exposed credentials
Scan all workloads to identify risks from exposed secrets, access keys, credentials, or weak passwords.
Let's analyze attack paths.
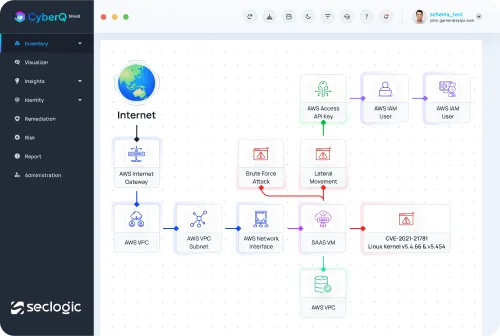
Advanced techniques allow for detailed detection of exposure chains and lateral movement leading to valuable assets, marking a significant advancement in CIEM.
Unnecessary punctuation in Toxic Combinations.
SecLogic scrutinizes cloud entitlements and risks, uncovering primary perils and enhancing cloud security effectively.
Connect in minutes without agents
Complete security for AWS, GCP & Azure Cloud. Meet your new partner in cloud security.