Get Comprehensive Visibility into AWS, Azure, and GCP
SecLogic delivers a cloud security platform that deploys within minutes and provides 100% coverage & contextual visibility
Secure your cloud
Cloud service providers follow a shared security responsibility model, which means security team maintains some responsibilities for security as applications, data, containers, and workloads are moved to the cloud, while the cloud provider takes some responsibility, but not all. Defining the line between your responsibilities and those of your providers is imperative for reducing the Risk of introducing vulnerabilities into your public, hybrid, and multi-cloud environments
Customer
Responsible for Security ‘in’ Cloud
- User Identity & Access
- Data
- Workload
- Application
- Network
- Cloud Configuration
Cloud Provider
Responsible for Security ‘of’ Cloud
- Foundational Services
- Hardware
- Virtualization Software
- Datacenter
Cloud Security & Compliance Management
Cloud is the sought after solution for data storage, infrastructure and services today. Most enterprises migrate to the Cloud following different models as alternatives; Public, Private or Hybrid and also service models of choice SaaS, IaaS or PaaS.
The vulnerabilities faced by the data stored on the Cloud or applications hosted there are self-explanatory, justifying the increasing importance of the penetration testing of cloud based applications, services and infrastructure. With a increasing number of enterprises migrating to the Cloud, the chances of breaches, threats and vulnerabilities increase day by day. Enterprises face unique challenges in protecting their resources over the various models of the Cloud.
Cloud security & compliance management comes with a unique challenge. The test strategy changes if the testing is to be done for the cloud service provider versus the Tenant. Since a Cloud is essentially a multi-tenant model; when the Cloud testing needs to be done for a particular tenant, it should avoid putting others at unease and also be conducted within the legal limits.
Cloud Security Essentials
Combination of identities - Humans & Machines in the Cloud
- Saas
- Iaas
Multi-Cloud Posture through {Single Pane of glass}
Tailored for Cloud Environments {IAAS, SAAS}
- Configuration Hardening
- Data Protection
- Identity Access Management
- Cloud Visibility and Discrepancy Detections
Niche features
- Contextually Assess, Detect & Remediation of vulnerabilities
- Hyper automation for plugging security holes
- Compliance check against global standards & benchmarks like CIS, NIST, CCM, GDPR, PIC etc.
- Zero Trust Access through least privilege roles/permissions
Why CyberQ Shield?
CyberQ Shield uniquely solves the cloud security problem by automatically identifying and remediating misconfigurations & vulnerabilities in the multi cloud environment
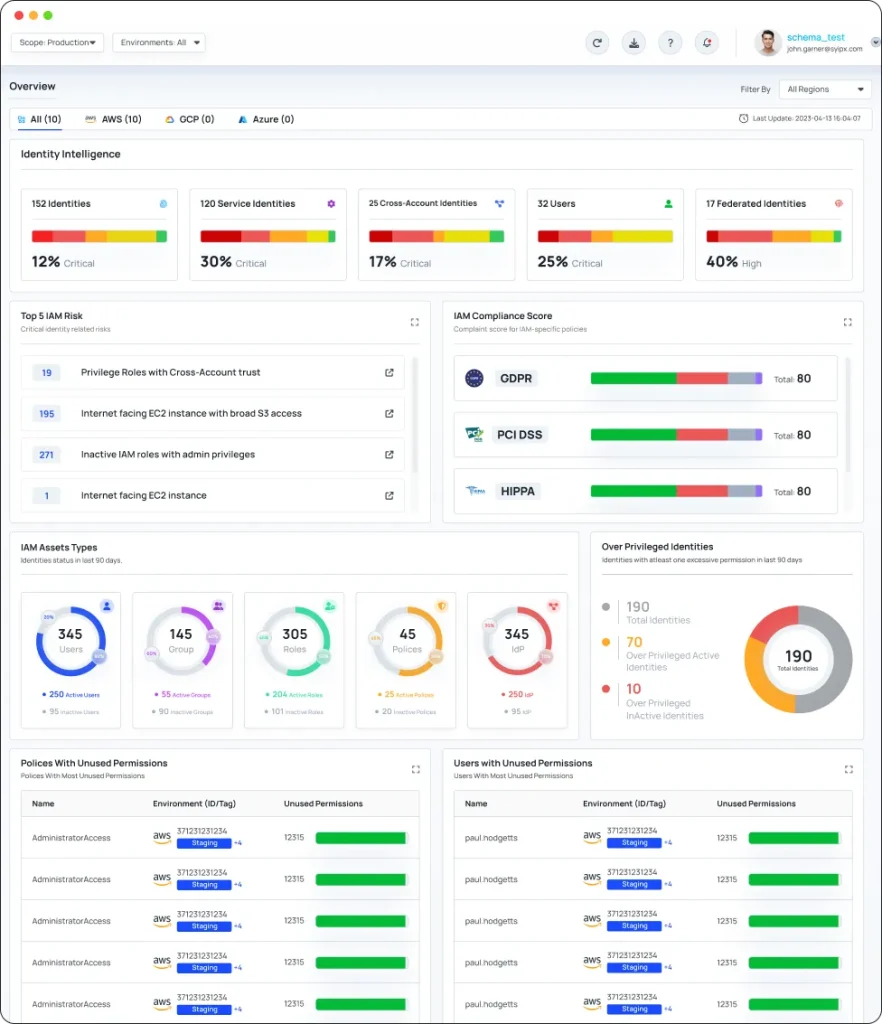
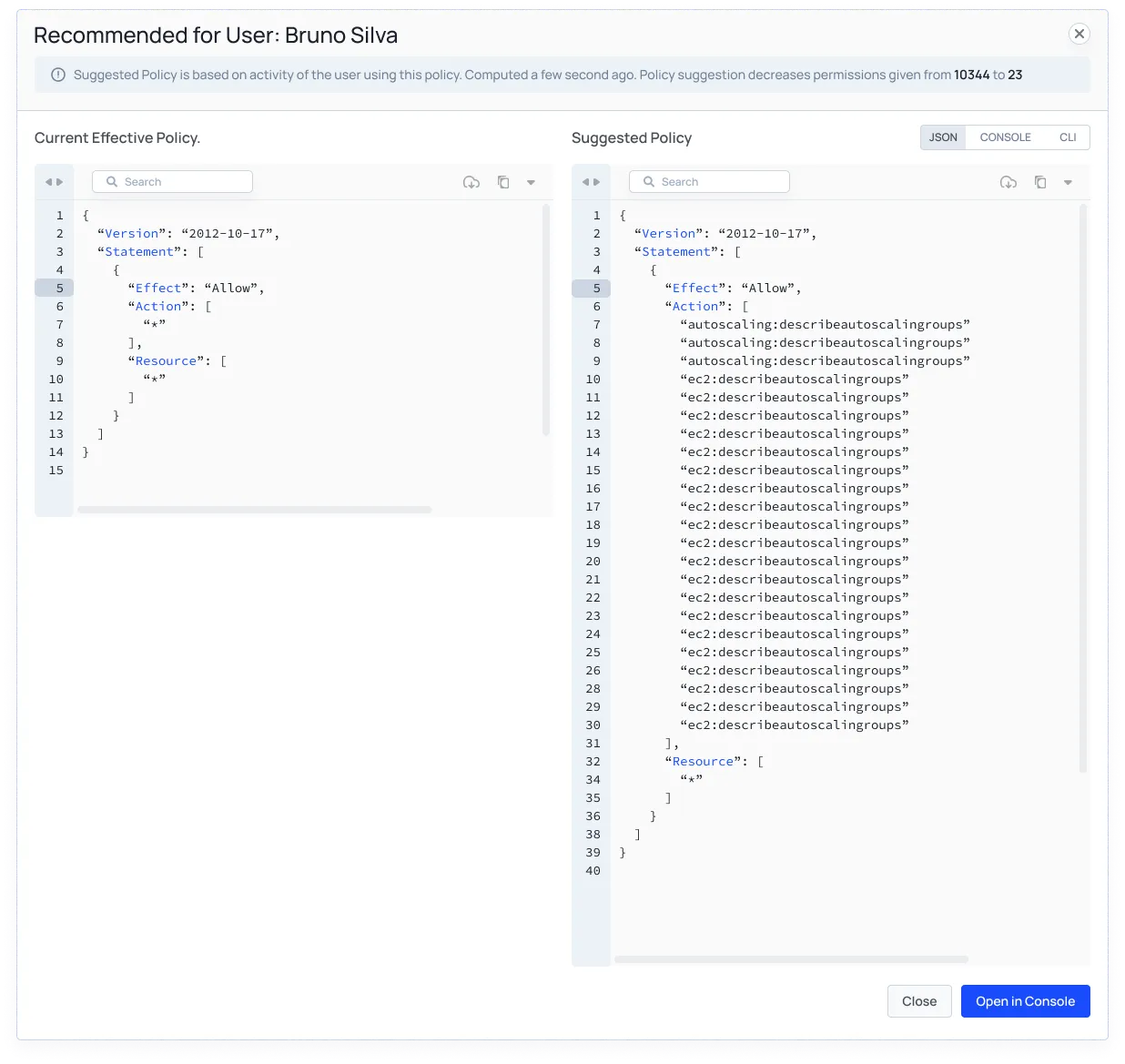
Automatically right size un-used IAM actions in you Cloud Environment(s)
Unlike agents, that sit inside cloud environments, CyberQ shield collects data externally & creates a complete risk profile of your cloud
- Stay ahead of the cloud security game with CyberQ Shield
- Protect your cloud like never before with CyberQ Shield
- Experience complete cloud risk assessment with CyberQ Shield
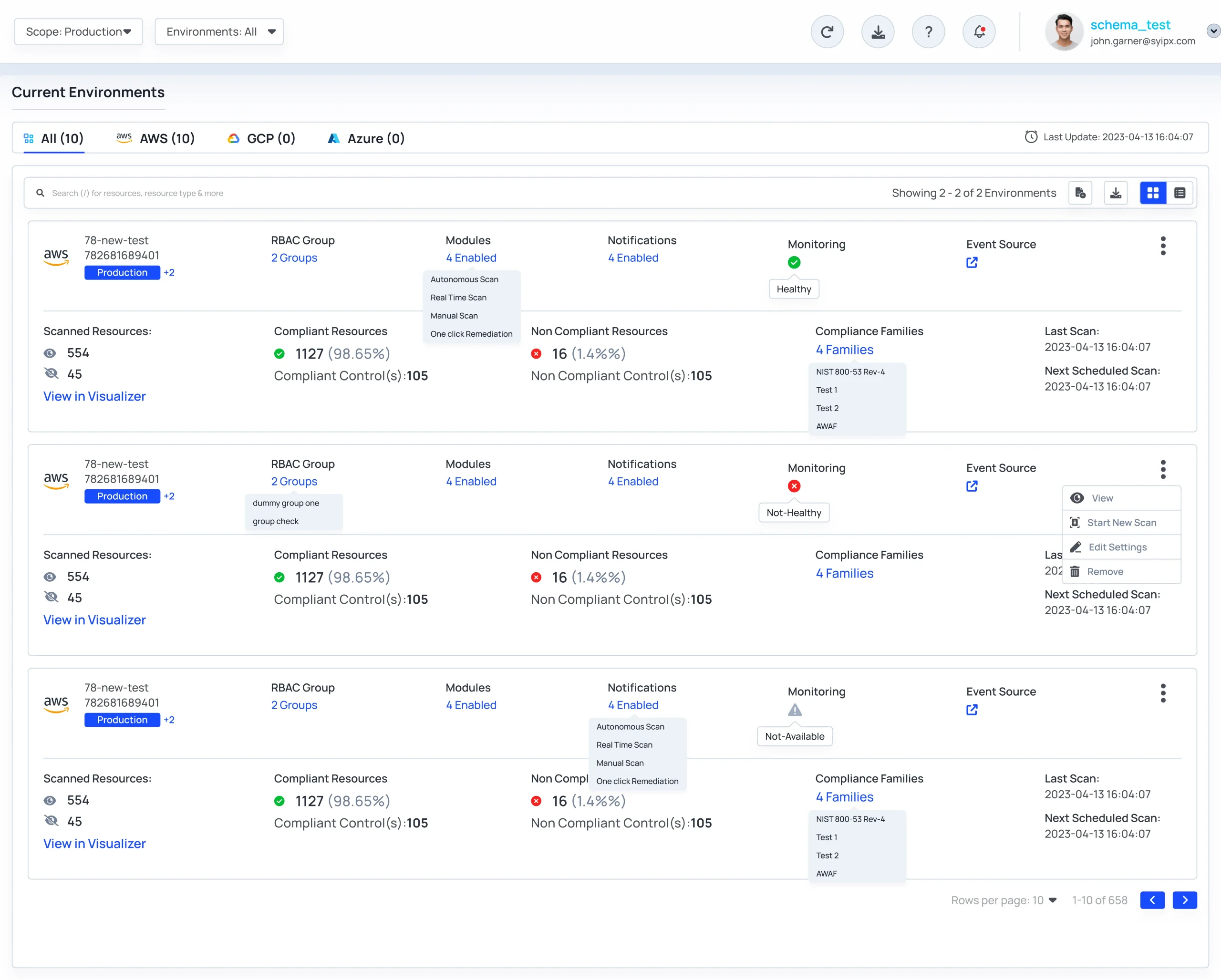
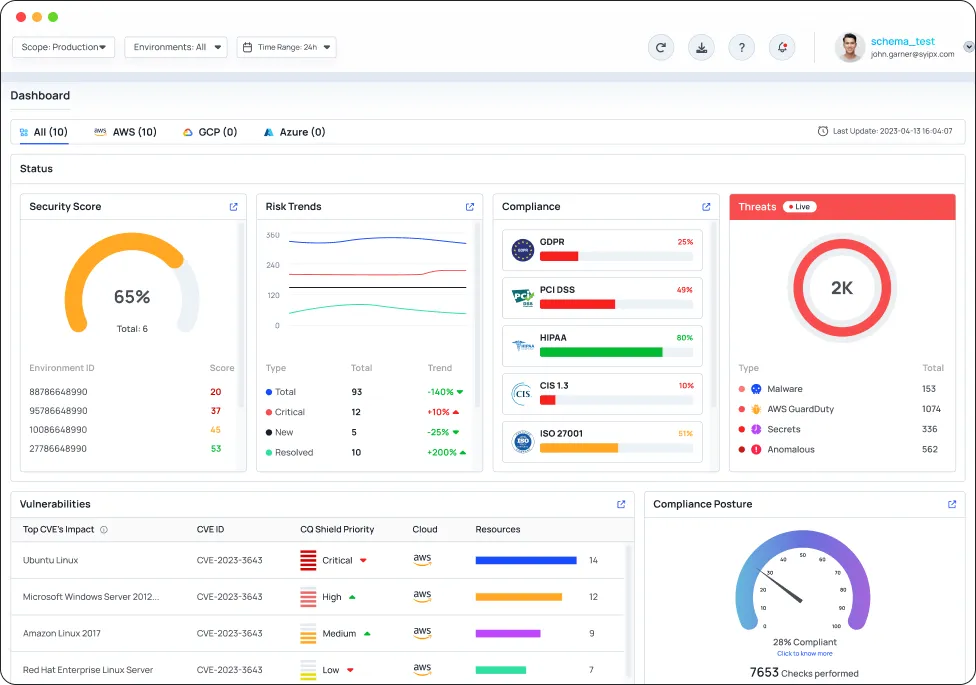
Connect Cloud Environment(s) & Scan for exposures
CyberQ Shield allows you to acheive complete visibility & coverage with no downtime and no impact on workloads or users
- Unleash your cyber defenses
- Protect your business with no downtime
- Total visibility and coverage, no disruption
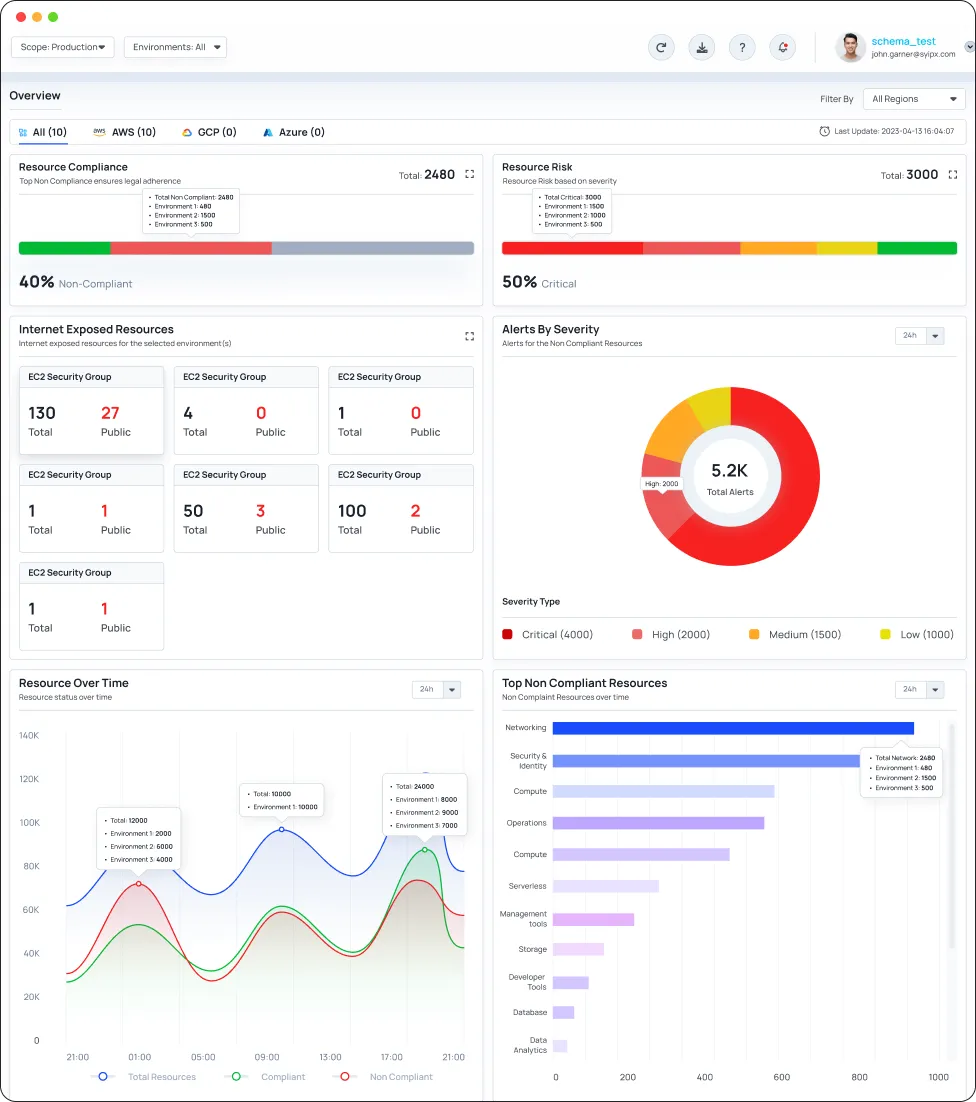
Mitigate Cloud Risk Automatically
CyberQ Shield Identify & Mitigate the most critical security risks, including resource misconfigurations, IAM risk, network exposures & much more
- Secure your digital footprint with CyberQ Shield
- Protect your assets against unforeseen cybersecurity threats
- Stay ahead of the curve with CyberQ Shield’s comprehensive security risk identification and mitigation
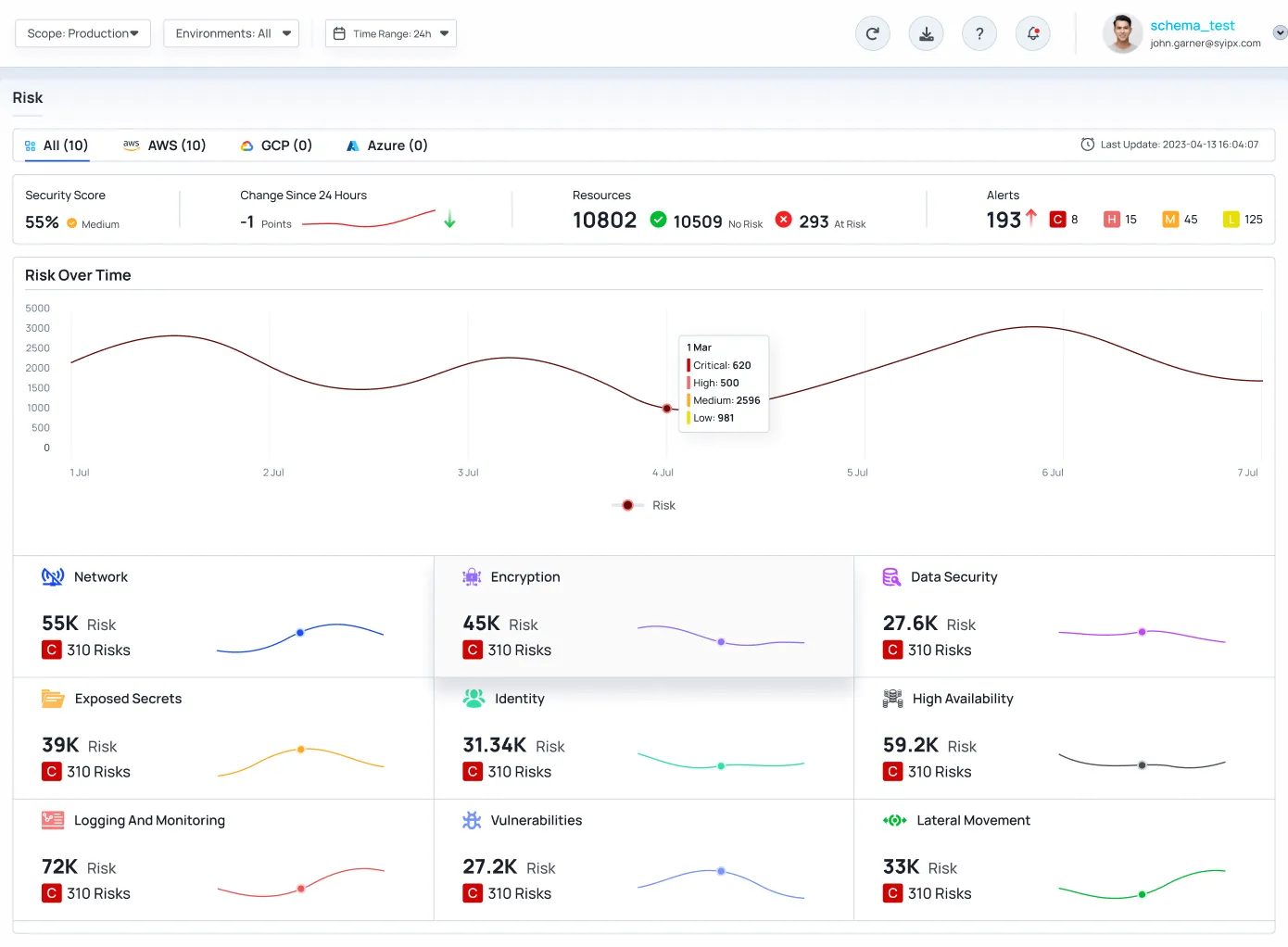
Key Features
CyberQ Shield is the agentless Cloud Security Platform, ideal for cloud-operating organizations seeking centralized visibility of their entire cloud environment, allowing security teams to prioritize actual risks for remediation.
Join us on your Cloud Security Journey.
CyberQ Shield is built from the ground up to align to customer challenges in managing cloud security
- 14-day free trial
- No credit card required
- Cancel anytime